Authentication and authorization in spring boot microservices top
Authentication and authorization in spring boot microservices top, How would you implement OAuth2 in Java Microservice Application top
$96.00
SAVE 50% OFF
$48.00
$0 today, followed by 3 monthly payments of $16.00, interest free. Read More
Authentication and authorization in spring boot microservices top
How would you implement OAuth2 in Java Microservice Application
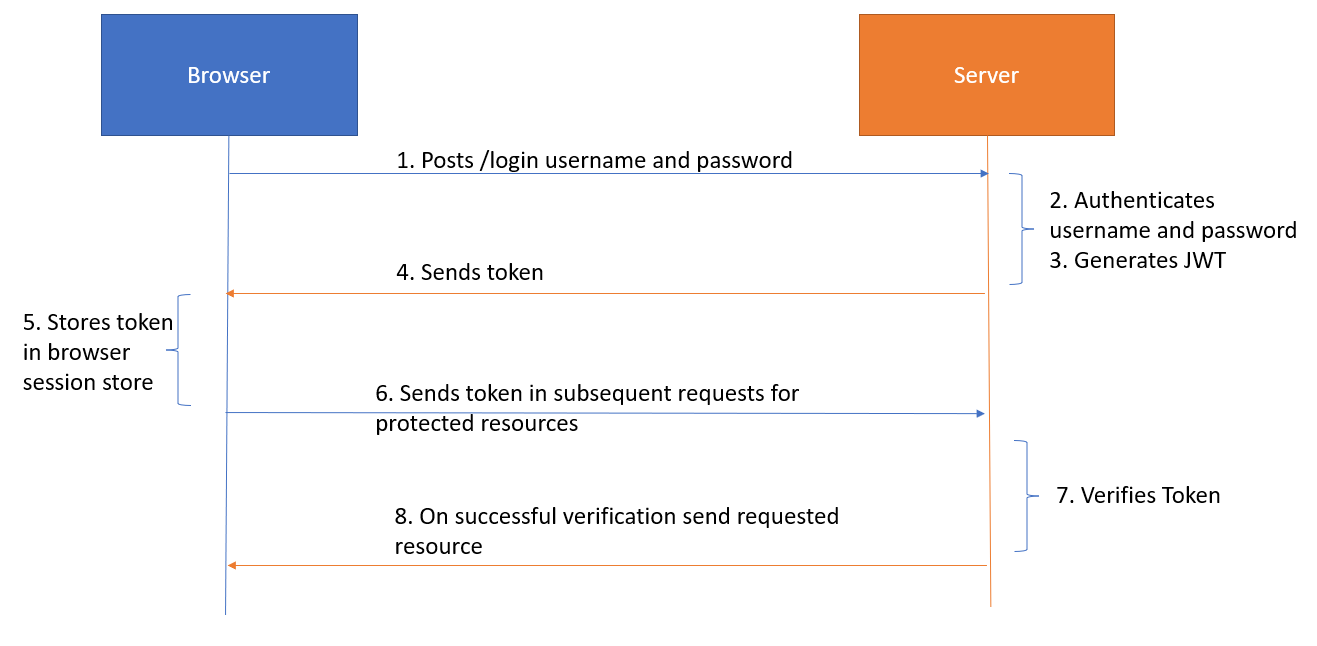
JWT Token Authentication in Spring Boot Microservices Spring
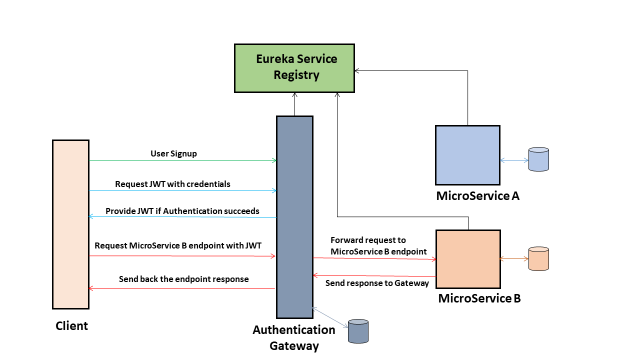
Microservices Security Using JWT Authentication Gateway Xoriant
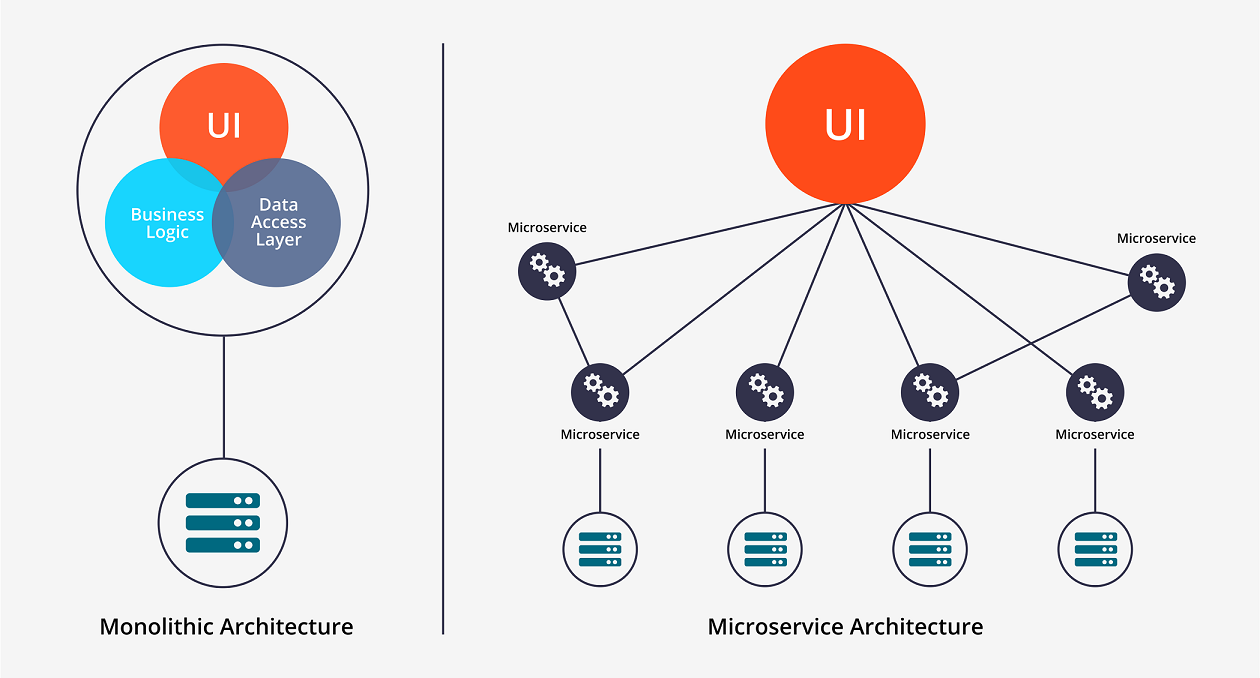
Building Microservices Using Spring Boot and Securing Them With
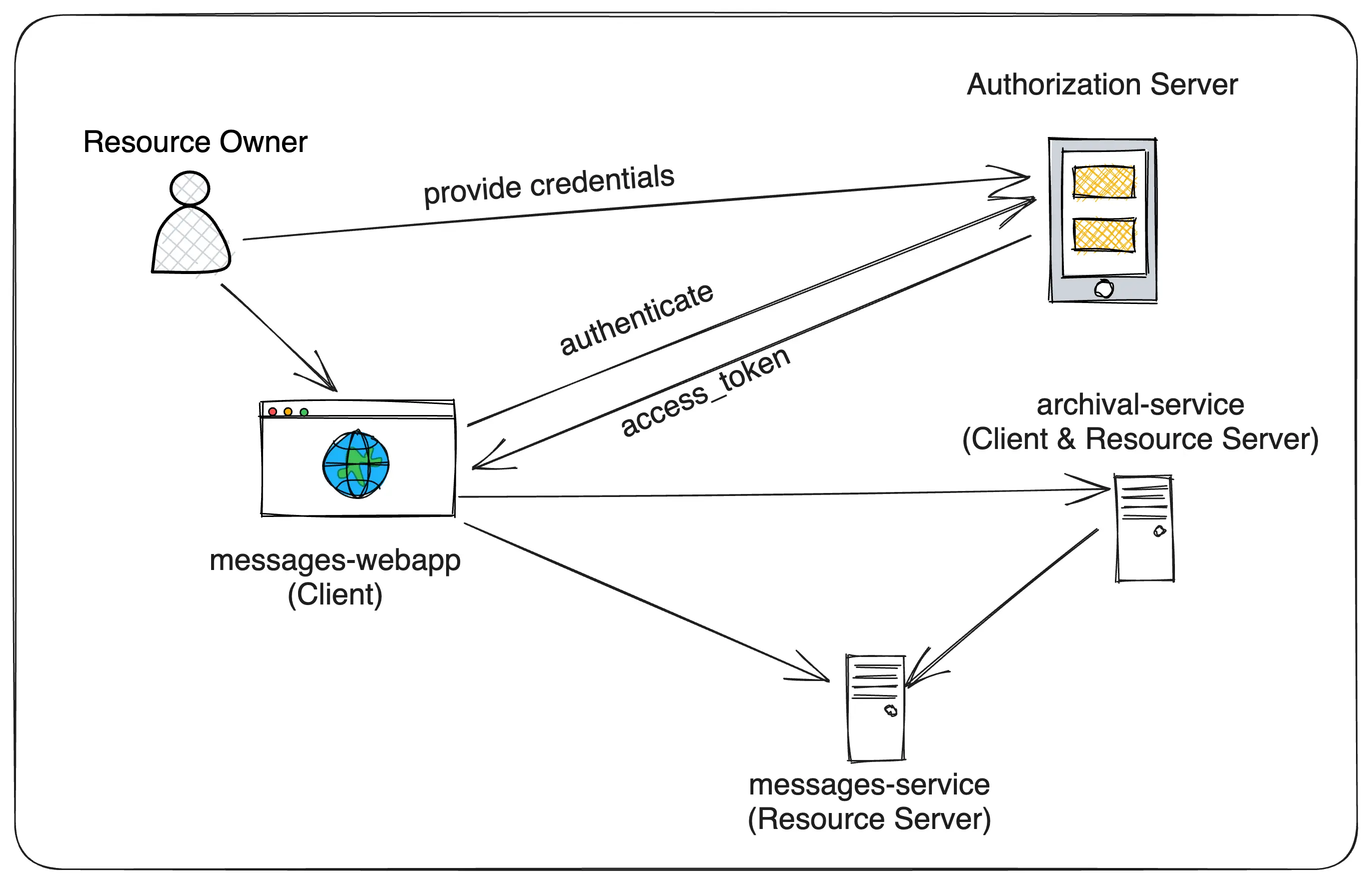
Spring Security OAuth 2 Tutorial 6 Microservices Sample
What is API Gateway Pattern in Microservices Architecture What
Description
Product Name: Authentication and authorization in spring boot microservices top
Microservices with Spring Boot Authentication with JWT and top, Microservices Authentication and Authorization using JWT Spring Boot Microservice JWT top, Authentication Authorization in Microservices Architecture top, Secure a Spring Microservices Architecture with Spring Security top, Spring Security in a microservices architecture Stack Overflow top, GitHub ahsumon85 secure spring boot microservice This repo we top, Spring Boot Authorization Creating an Authorization Server for top, Microservice authorization using JWT using Spring Boot top, Securing REST microservices with Spring Security Stack Overflow top, Securing Services with Spring Cloud Gateway top, Securing Microservices with Spring Cloud Security top, How to Implement Oauth2 Security in Microservices DZone top, Applied Sciences Free Full Text Authentication and top, Spring Microservices Security Best Practices top, How would you implement OAuth2 in Java Microservice Application top, JWT Token Authentication in Spring Boot Microservices Spring top, Microservices Security Using JWT Authentication Gateway Xoriant top, Building Microservices Using Spring Boot and Securing Them With top, Spring Security OAuth 2 Tutorial 6 Microservices Sample top, What is API Gateway Pattern in Microservices Architecture What top, Part 2 Microservices security with OAuth2 Piotr s TechBlog top, JWT Token Authentication in Spring Boot Microservices Spring top, Securing Spring Microservices with Keycloak Part 1 JDriven Blog top, GitHub akhuntsaria spring boot api gateway API authentication top, java Spring boot user authenticate with keycloak microservices top, Authentication and Authorization in Microservices Architecture top, Building microservices part 3. Secure API s with OAuth 2.0 Callista top, Secure Reactive Microservices with Spring Cloud Gateway Okta top, Spring Cloud Gateway security with JWT ORIL top, Spring Boot Token based Authentication with Spring Security JWT top, Securing Spring Boot Microservices Using Keycloak Client top, java How to secure communication between 2 Spring Boot top, Authentication and Authorization in Microservices Harshit Jain top, Applied Sciences Free Full Text Authentication and top, Spring Cloud Gateway With Spring Security top, Microservices with Spring Boot Authentication with JWT and top, Microservices Authentication and Authorization With Keycloak top, Microservices with Spring Boot Oauth2 Authorization Identity top, Spring Boot Microservices with Keycloak Dumi s Blog top, Authentication in Microservices Approaches and Techniques Frontegg top, Advanced Microservices Security with Spring and OAuth2 DZone top, Microservices with Spring Boot and Spring Cloud Second Edition top, Spring Boot Token based Authentication with Spring Security JWT top, Securing microservices with Keycloak coffeehack.io top, Jmix in microservice solution. Why not Ideas Jmix top, Securing your microservices with OAuth 2.0. Building Authorization top, Chapter 7. Securing your microservices Spring Microservices in top, Authentication Authorization in Microservices Architecture top, How to Properly Implement Authorization in a Microservice top, Sensors Free Full Text Applying Spring Security Framework with top.
Microservices with Spring Boot Authentication with JWT and top, Microservices Authentication and Authorization using JWT Spring Boot Microservice JWT top, Authentication Authorization in Microservices Architecture top, Secure a Spring Microservices Architecture with Spring Security top, Spring Security in a microservices architecture Stack Overflow top, GitHub ahsumon85 secure spring boot microservice This repo we top, Spring Boot Authorization Creating an Authorization Server for top, Microservice authorization using JWT using Spring Boot top, Securing REST microservices with Spring Security Stack Overflow top, Securing Services with Spring Cloud Gateway top, Securing Microservices with Spring Cloud Security top, How to Implement Oauth2 Security in Microservices DZone top, Applied Sciences Free Full Text Authentication and top, Spring Microservices Security Best Practices top, How would you implement OAuth2 in Java Microservice Application top, JWT Token Authentication in Spring Boot Microservices Spring top, Microservices Security Using JWT Authentication Gateway Xoriant top, Building Microservices Using Spring Boot and Securing Them With top, Spring Security OAuth 2 Tutorial 6 Microservices Sample top, What is API Gateway Pattern in Microservices Architecture What top, Part 2 Microservices security with OAuth2 Piotr s TechBlog top, JWT Token Authentication in Spring Boot Microservices Spring top, Securing Spring Microservices with Keycloak Part 1 JDriven Blog top, GitHub akhuntsaria spring boot api gateway API authentication top, java Spring boot user authenticate with keycloak microservices top, Authentication and Authorization in Microservices Architecture top, Building microservices part 3. Secure API s with OAuth 2.0 Callista top, Secure Reactive Microservices with Spring Cloud Gateway Okta top, Spring Cloud Gateway security with JWT ORIL top, Spring Boot Token based Authentication with Spring Security JWT top, Securing Spring Boot Microservices Using Keycloak Client top, java How to secure communication between 2 Spring Boot top, Authentication and Authorization in Microservices Harshit Jain top, Applied Sciences Free Full Text Authentication and top, Spring Cloud Gateway With Spring Security top, Microservices with Spring Boot Authentication with JWT and top, Microservices Authentication and Authorization With Keycloak top, Microservices with Spring Boot Oauth2 Authorization Identity top, Spring Boot Microservices with Keycloak Dumi s Blog top, Authentication in Microservices Approaches and Techniques Frontegg top, Advanced Microservices Security with Spring and OAuth2 DZone top, Microservices with Spring Boot and Spring Cloud Second Edition top, Spring Boot Token based Authentication with Spring Security JWT top, Securing microservices with Keycloak coffeehack.io top, Jmix in microservice solution. Why not Ideas Jmix top, Securing your microservices with OAuth 2.0. Building Authorization top, Chapter 7. Securing your microservices Spring Microservices in top, Authentication Authorization in Microservices Architecture top, How to Properly Implement Authorization in a Microservice top, Sensors Free Full Text Applying Spring Security Framework with top.
Authentication and authorization in spring boot microservices top
- authentication and authorization in spring boot microservices
- authentication entry point spring security
- authentication in spring
- authentication in spring boot
- authentication java spring
- authentication spring boot
- authentication spring boot rest
- authentication spring security
- authentication with spring security
- authenticationentrypoint example